Can Someone Hack My Computer Through WiFi? In the ever-evolving landscape of technology, the potential threat of unauthorized access to your computer through Wi-Fi is a real concern. The idea of a stranger gaining access to your personal information is undoubtedly unsettling.
However, fear not, as there are effective measures you can take to safeguard your digital fortress.
Cyber attackers often exploit vulnerabilities when devices connect to shared networks, such as public Wi-Fi hotspots. Strengthening your defenses against such threats involves enhancing your firewall and antivirus systems. In this user-friendly guide, we’ll unravel the intricacies of how hackers can infiltrate your computer through Wi-Fi and, more importantly, equip you with practical steps to thwart their attempts.
Join us as we demystify the world of cyber threats and empower you to fortify your online security. Let’s dive in and arm you with the knowledge to protect your digital realm.
In this article, we’ll show exactly how can Someone Hack My Computer Through WiFi.
also check one of my related post links here: Can You Upgrade a Laptop CPU
Quick Answer: Can someone hack my computer through Wifi?
Yes! It’s within the realm of possibility for someone to hack into your computer via a WiFi connection, particularly when using an unsecured network. The vulnerability arises as hackers exploit weaknesses or introduce malware through such unsecured channels.
Shield your computer by fortifying your defenses—set a robust WiFi password, and ensure your operating system and antivirus software are always up to date. These simple yet crucial steps act as a digital shield against potential cyber threats. Your computer’s security is in your hands—empower it with these protective measures.
How do Hackers infiltrate Computers Through Local WiFi?
It’s a genuine concern, and understanding the process is key to safeguarding your digital space. Hacking becomes a walk in the park when the target computer is in close quarters with the hacker’s device.
Consider this scenario: your neighbor effortlessly piggybacks onto your WiFi, enjoying free internet at your expense. Picture yourself at a cafe or hotel, connecting to what you believe is free WiFi, only to discover it’s been compromised, making you an unwitting target along with everyone else.
Even your workplace’s WiFi isn’t immune to potential hacks. It’s not just computers like Macs or PCs; your trusty smartphones, whether iPhones or Androids, connected to WiFi, are also vulnerable.
Now, let’s delve into what hackers can unleash when they physically tap into the WiFi you’re using. Stay tuned for insights into the covert world of digital intrusion and discover how to fortify your online defenses.
Man-in-the-Middle attack
Let’s unravel the mysteries behind the Man-in-the-Middle attack, a technique frequently employed by cyber adversaries to compromise your online security. If you’re connected to the internet at home through cable, DSL, or fiber-optic services, chances are you have a router. Here’s a simplified breakdown:
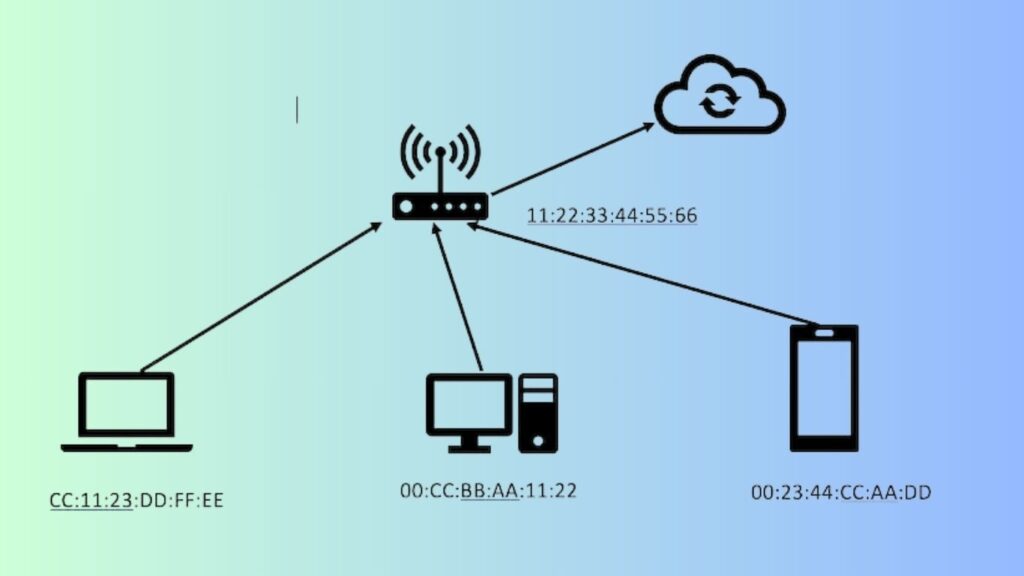
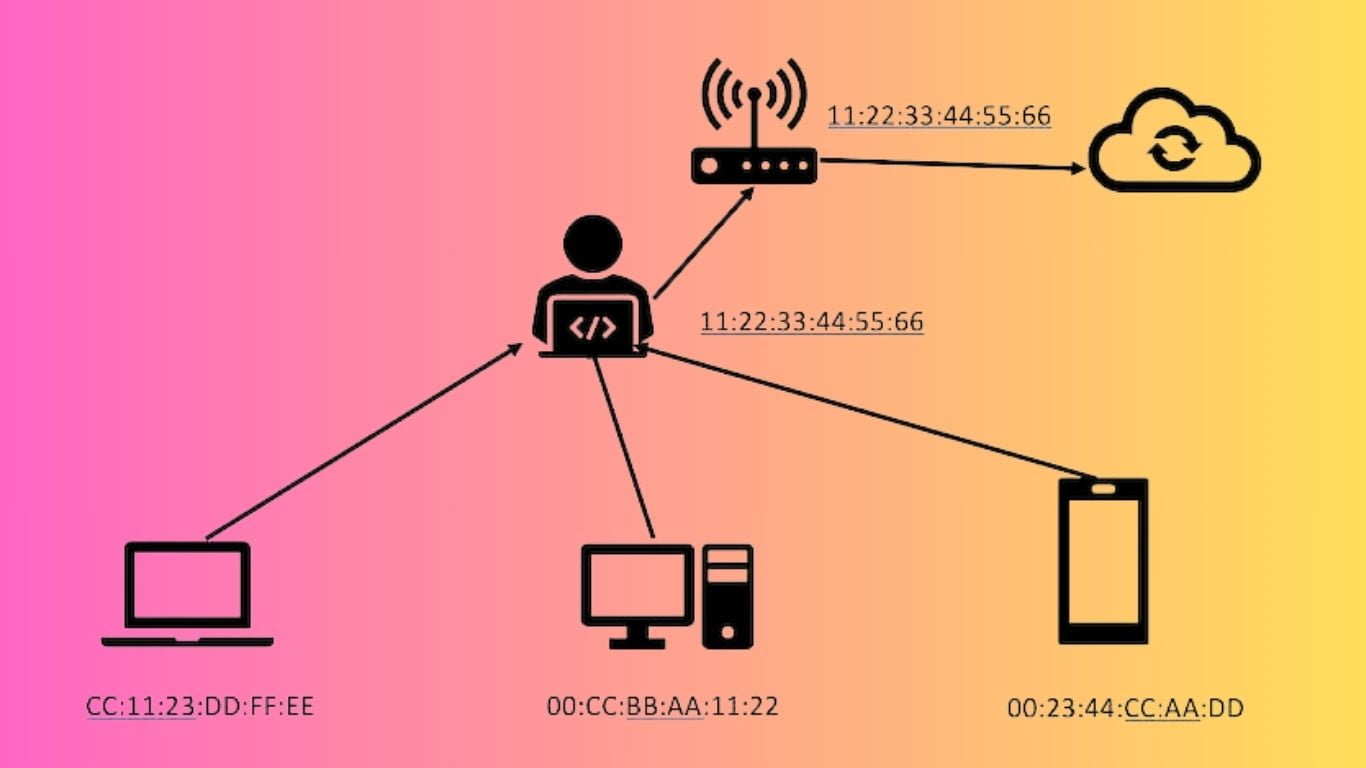
In the digital landscape, safeguarding your home WiFi network is paramount. Imagine this: when a hacker infiltrates your local WiFi router, they go a step further by identifying the router’s unique MAC address. Subsequently, the hacker ingeniously alters their computer’s MAC address to mirror that of your router, creating a deceptive mirroring effect (as illustrated by the 11:22:33:44:55:66 sequence in the accompanying image).
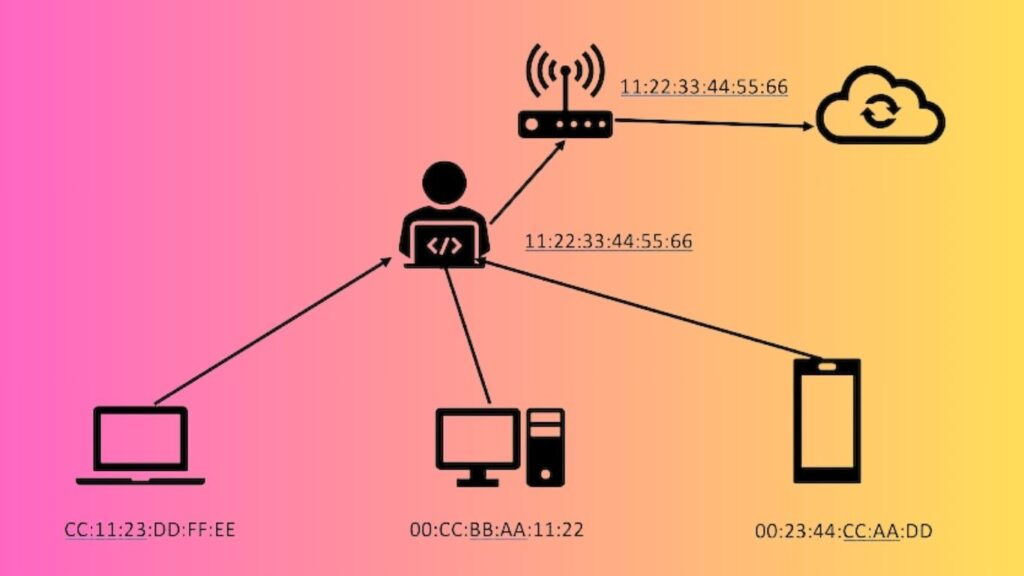
This manipulation allows the hacker to position themselves as a discreet observer, intercepting data as it traverses between devices and the router. This technique, commonly known as a “man in the middle” (MITM) attack, poses a tangible threat to your network’s security.
To counteract such potential breaches, it’s crucial to fortify your WiFi network against unauthorized access. Stay vigilant and implement robust security measures to protect your digital haven from these cyber threats. Understanding the intricacies of MAC address manipulation is a crucial step toward creating a resilient defense against hackers seeking to exploit vulnerabilities in your network.
How the router can be hacked?
Safeguarding your router from cyber threats is crucial, and it starts with securing the front door. If your router lacks password protection or has a common or default password like ‘12345678’, it’s like an open invitation for cybercriminals. Additionally, an outdated authentication protocol, such as the vulnerable WEP (Wired Equivalent Privacy), can make hacking your router a walk in the park.
To bolster your router’s defenses, begin by changing its login credentials. Opt for a strong, lengthy password with at least 15 to 20 characters, making it significantly more challenging for hackers to crack. Remember to customize your SSID (Router or network name) to avoid giving away your router type; longer and more intricate names enhance your router’s WPA security.
Old authentication protocols like WEP and the relatively less secure WPS (Wireless Protected Setup) can be exploited by hackers. While WPA (Wireless Protected Access) provides a higher level of security, the encryption method matters. WPA with TKIP encryption is somewhat vulnerable, whereas the latest protocols, WPA3 and WPA2 with the AES encryption algorithm, offer the most robust protection.
For enhanced authentication strength, it’s recommended to update routers from WEP, WPS, and WPA to the more secure WPA2 or WPA3 protocols. Although no connection is entirely immune to cyber threats, advanced protocols like WPA and beyond add an extra layer of security, deterring hackers with substantial resources from targeting your network, unless, of course, you’re a high-profile target.
Stay ahead in the cybersecurity game by fortifying your router with the latest and most secure protocols available.
How to tell if someone hacked your router?
Detecting signs of a hacked router is crucial for maintaining your online security. A clear red flag is the presence of unfamiliar devices connected to your local WiFi network. Understanding that a hacker needs to infiltrate your WiFi network to execute a man-in-the-middle (MITM) attack, it becomes vital to identify and eliminate any unauthorized connections.
Checking your router settings is a straightforward method to unveil connected devices. Many routers offer the option to view all connected devices and even kick them out if necessary. Alternatively, employing a network scanner app simplifies the process. Take, for example, the user-friendly app called Fing, available across iOS, Android, macOS, and Windows platforms.
What makes Fing stand out is its user-friendly interface and the ability to scan for open ports. This feature proves invaluable in revealing potential vulnerabilities. During my scan using Fing, I discovered that certain features, such as remote desktop and screen sharing, were enabled on my MacBook Pro, posing a security risk.
Identifying and addressing these issues promptly can be the key to securing your network and thwarting potential cyber threats. Stay proactive, stay secure.
How to protect from an MITM attack
Shielding yourself from a Man-in-the-Middle (MITM) attack is crucial, especially when using public WiFi networks like those in coffee shops or hotels. Unlike your home network, where you can scan for unfamiliar devices, public networks may be compromised without your knowledge. The go-to solution for maintaining your privacy in such scenarios is to employ a Virtual Private Network (VPN).
When you connect to a VPN, your computer or phone establishes a secure, encrypted channel with the VPN server. All your requests are then routed through this server, which acts on your behalf and returns the results. To an outsider, it appears as if your computer is sending and receiving random data. Even if a hacker attempts to intercept information, they won’t discern whether you’re accessing Google.com or MacMyths.com.
Choosing the right VPN software is crucial, and here are some best practices to follow. Firstly, steer clear of free VPNs, as they often come with significant limitations. Test the speed of different VPNs, as performance can vary. Finally, prioritize reputable providers because, with a VPN, the server becomes the new middleman in your online transactions.
I recommend NordVPN for its exceptional speed and affordability. It’s compatible with various platforms like macOS, Windows, Linux, iOS, and Android. If you use my NordVPN affiliate link, you can enjoy a substantial discount on a three-year plan for up to 6 devices, ensuring robust protection for your online activities. Stay secure, stay connected with confidence.
Can Someone Hack My Computer Through WiFi: FAQ
1. Is it possible for someone to hack my home computer?
Absolutely, yes. Your home computer is vulnerable to hacking if you don’t have proper security measures in place. Hackers can exploit weaknesses in your network connection, gaining unauthorized access to your system. To safeguard against this, make sure your Wi-Fi is secured with a robust password, keep your software up-to-date, and install a reliable antivirus program on your system.
2. Can I monitor someone using my Wi-Fi?
While it is technically possible to monitor someone using your Wi-Fi, it’s essential to note that such actions are both unethical and illegal. Through router logs and third-party network monitoring tools, you can check their online activities.
However, it’s crucial to respect privacy laws and not engage in such behavior. Parents, for instance, may use these tools responsibly to supervise their children’s internet usage and prevent exposure to inappropriate content. Always ensure you abide by legal and ethical standards when using monitoring tools.
Conclusion
In today’s life technology has gone so far that everyone uses it a lot but sometimes issues come up like “Can Someone Hack My Computer Through WiFi” so I have decided to fix this issue here is the solution.
To bolster your online security, consider incorporating these essential tools into your digital arsenal:
When navigating the digital landscape, exercise caution, especially when connecting to public WiFi networks. If you lack VPN protection on your laptop or smartphone, it’s advisable to steer clear of public WiFi or, at the very least, refrain from engaging in sensitive activities like making purchases or entering passwords.
For those keen on deepening their understanding of security, I recommend exploring Udemy’s comprehensive course on ethical hacking. Knowledge is a powerful defense, and this course provides valuable insights into ethical practices for safeguarding your digital world.